There are a lot of choices when we want to pen test an application.
- We can create a specific program to do this.
- We can use an existing one.
- We can modify (or... fork) an existing.
Maybe, the ideal is to create your own program for attack, but again,
this, has some drawbacks:
- You don't have to reinvent the wheel.
Is there is something we can do about it?
Hmm, I suppose yes! There many ways to hide the program from an anti-virus. I will present two of them.
But, before we start, we must say something about how anti-viruses recognize threats. Actually there many ways to do this, but a general rule (that is used in most of cases) is the following: Using an one-way hash function they encoded a known executable Malware file into a smaller but unique code and they store this code into its internal database. When we try to execute a program they transform our executable (using the same hash function) into a code and they check if this code exist in its database. If it exists they consider the executable as a threat and they block it.
So, our goal is to change the executable (or some bytes of it) in such way that will produce a totally new hashed code that is not exists in anti-virus database. If we did this then our executable will not be considered as a legitimate program!
Method 1, the easy one
In this method we will change some bytes in the executable in order to hide it from an anti-virus. We must be very careful here because it is very easy to change the behavior of the executable or even worst to destroy it (make it impossible to run). The principle that is behind this approach is the following:
Almost every program has in its code some software interrupts that used by debuggers to interrupt program execution. Software interrupts are useful to programmers when they need to put break points to pause execution at a specific address in order to review the code and/or data. With software interrupts this task can be done without overwriting programs code. But... we are not in a debugging status here. We don't need these interrupts. We can replace them with something else, with some... nothing: The NOP mnemonic!
Lets be more specific:
Software Interrupt represented by the assembly mnemonic INT 3 which is the CC instruction.
NOP is represented by the 90 instruction.
Thus, if we change every CC with 90 then we will have a totally different executable with exactly the same behavior. We can do this from simple hex editor. In my example I choose to use the very best windows editor ultraedit.
I open the nc.exe with ultra edit in hex mode and I tried to find some CC instructions.
The above CC instructions must be replaced by 90.
To be honest, I search for every triple of "CCCCCC" and I replace it with "909090".
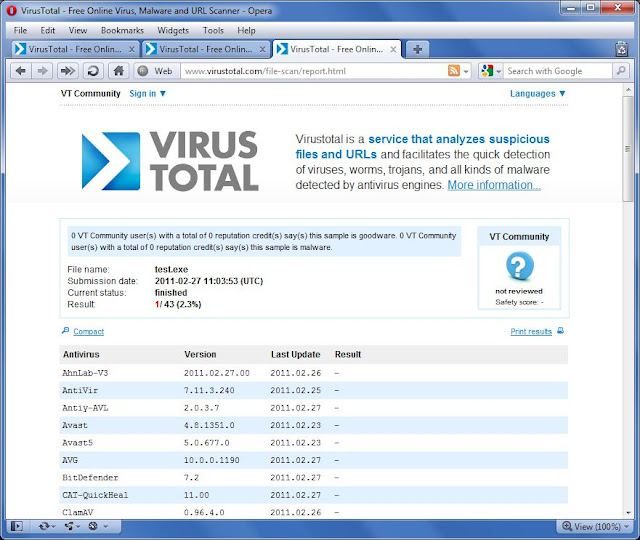
Now lets test our results. I will use the well known http://www.virustotal.com site to test the programs for Malware behaviour. First I check the original Netcat program (nc.exe):
Let's try my ncWithNOPs.exe to see what happens:

Method 2: Modifying the source code
This method is more challenging but requires to have the source code and of course to know how to program! Ideal candidate for this method are all Open Source programs. Netcat is not an exception. Its source code that will be run on Windows can be found here.
We can get the source code, modifying in such way that will produce a different executable with the same functionality. I used this method by making changes to the source code of Netcat without changing its actual behavior. The changes in source code I made was:
1. I change the name of any constant in the program (using global replace).
2. I change the name of any variable in the program (using global replace).
3. I change the name of any function in the program (using global replace).
4. I add more parameters to many functions that did nothing.
5. I change loops. For example I change While-loops to their For-loops equivalent.
6. I compile the program with no optimizations. This is because I wanted to keep all my "dummy" variables/parameters or loops intact.
7. I didn't use any packer in purpose. Many anti-viruses dislike them!
Finally I recompile and test the program in order to check that retains its initial functionality. I rename the program to "test.exe" and I put it to the virus-total. The results were good:
Remarks
I will not provide you the final executable as a minimum defense line against script kiddies. If you know how to program it is VERY EASY to implement the above steps in the original source files.
References
http://dl.packetstormsecurity.net/papers/virus/Taking_Back_Netcat.pdf
Sources
You can download the original source code for Netcat for Windows from here.




thank for share with us this important matter.
ReplyDeleteMalware is the most familiar name for every computer user. Every user know what is malware. It is a popular virus for every computer, laptop and website. This virus entered by using fake software and browsing many bad blog site. It can occurred many problem in our computer. It also can damage our blog site. So before affected by malware we should make perfect protection from this virus. Then we need use anti-malware software. Malwarebytes Anti-Malware Premium is one of the kind of software
Free Software